 [ITFIND] 클라우드 서비스 보안기술 동향 - CASB
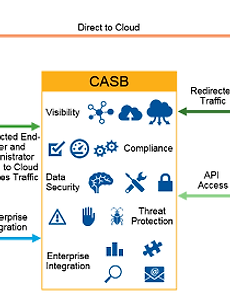
■ 클라우드 서비스 접속 보안 브로커 (Cloud Access Security Broker: CASB) - Gartner가 2014년 향후 정보보호분야 10대 유망기술 중 1위로 선정한 것 - 클라우드 서비스 이용자와 클라우드 서비스 사이에 위치하여 독립적으로 보안 기능을 수행 - 클라우드 서비스 이용에 대한 접근 통제, 내부정보 유출방지, 이상탐지, 로깅, 감사 등의 보안 기능을 수행 1. CASB의 개념 - 필요에 따라 서비스 형태로 제공하여 다양한 보안 위협에 대비할 수 있다. - 가시성, 준수, 위협 방지, 데이터 보안 4가지를 중요하게 여기고 있으며, 이러한 바탕에 접근 통제, 내부정보 유출방지, 이상탐지, 로깅, 감사 등의 보안 기능을 수행한다. ○ CASB 기능 - 클라우드 서비스 검색 및 ..
2017. 5. 17.
[ITFIND] 클라우드 서비스 보안기술 동향 - CASB
■ 클라우드 서비스 접속 보안 브로커 (Cloud Access Security Broker: CASB) - Gartner가 2014년 향후 정보보호분야 10대 유망기술 중 1위로 선정한 것 - 클라우드 서비스 이용자와 클라우드 서비스 사이에 위치하여 독립적으로 보안 기능을 수행 - 클라우드 서비스 이용에 대한 접근 통제, 내부정보 유출방지, 이상탐지, 로깅, 감사 등의 보안 기능을 수행 1. CASB의 개념 - 필요에 따라 서비스 형태로 제공하여 다양한 보안 위협에 대비할 수 있다. - 가시성, 준수, 위협 방지, 데이터 보안 4가지를 중요하게 여기고 있으며, 이러한 바탕에 접근 통제, 내부정보 유출방지, 이상탐지, 로깅, 감사 등의 보안 기능을 수행한다. ○ CASB 기능 - 클라우드 서비스 검색 및 ..
2017. 5. 17.